CPTS and Improving Your Methodology
Intro
While I’m still definitely unemployed, I completed Hack the Box’s CPTS exam a couple of days ago, and, although stressful at times, it was a fun experience! With < 300 people certified, most posts after the CPTS tend to be reflections on the course and general reviews, but quite frankly, I think these posts from xre0us and madf0x and videos from bmdyy and CryptoCat do excellent jobs of covering what you need to know going into the exam. The point of me writing is less to talk about CPTS (which is something I will touch on), but more to talk about preparation going into it, and how my experience with the course, exam, and outside prep really helped build good habits with my methodology.
- Intro
- CPTS Explanation (any%)
- Methodology is King
- Okay okay back to the exam
- Some Qualms
- FAQ
- On a completely arbitrary scale, how would you rate the difficulty from 1 -10? Quality from 1 - 10?
- How many hours did you spend on the exam?
- How does CPTS help hiring?
- How can I pick your brain so I’m also ready for it?
- How do I know when I’m ready for Flags 1 and 9?
- Ok but actually
- How are you doing?
CPTS Explanation (any%)
The Course
A quick rundown of what CPTS is:
- CPTS is the second certification Hack The Box has developed and is functionally a competitor to entry-level certifications such as OSCP
- Taking the exam requires 100% completion of the course at any given point in time, which includes 28 different sections on various topics, and interactive exercises within each section.
- The exam is a 10-day, unproctored assessment where you are to conduct a full penetration test for a small business environment. Successful exam completion includes submitting 12/14 flags in the environment, and a legitimate report that includes an executive summary, findings, remediations, etc.
- The cost of CPTS (course + exam) will depend on the method you choose to pay for the course. I had a student subscription, which is $8 a month for all of the course material (genuinely a steal). xre0us says that getting a month of platinum subscription and another month of gold comes out to a course cost of $106 over 2 months. An exam voucher costs $210, but comes with a free retake.
When I first heard about the cert, I had no intention to actually complete the whole thing. I already had beginner to intermediate experience with CTFs, was able to complete easy and sometimes medium boxes consistently, and just felt pretty okay with my overall skill set. The only reason I ended up starting with Hack The Box Academy in the first place was completing the CBBH (Certified Bug Bounty Hunter) course, because I felt that web exploitation was a weak point for me (don’t tell the employers that, they make faces at me when I’m honest about it). After that, I started working through the Windows Privilege Escalation and Active Directory Enumeration and Attacks modules because I wanted to revise them, and I slowly began working through the CPTS material.
I can’t say exactly how long it took me to complete the CPTS material because of the overlap in modules between CPTS and CBBH, but my rough estimate is that I took ~1 month on CPTS altogether, given that I already had experience with a majority of the material. That said, I still managed to pick up a lot of tricks, solidify my understanding of certain concepts, and have a more holistic understanding of some vulnerability classes and how they may pop up.
The Exam
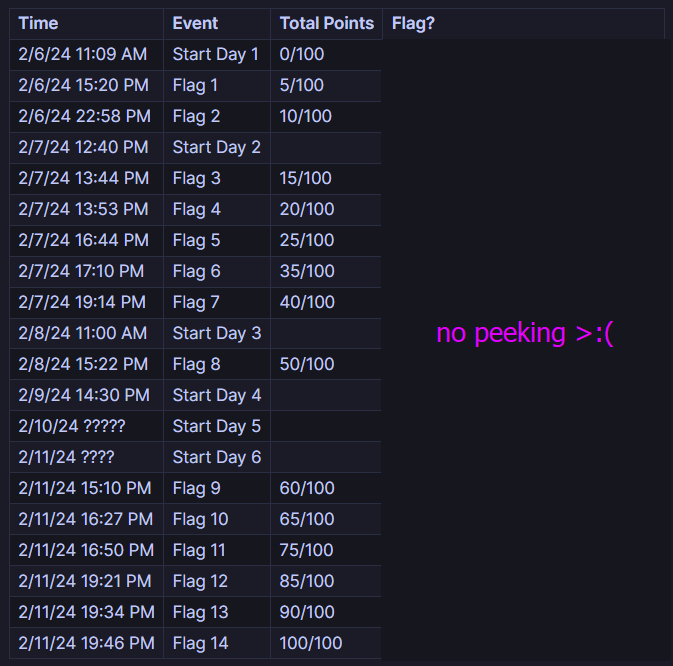
When you’re ready to take the exam, all you do is buy a voucher, click “Enter Exam”, and you’re straight in it. I started my exam on February 6th, and collected all 14 flags by the 11th. I took an additional 3 days to write the report, and I finally got my results on February 25th (yes, a long wait). I kept a log of when I started working on certain days, and when I got flags, but note that my experiences will not necessarily reflect yours, and moreso indicate how quickly I managed to pick up on things.
I think everything that can and needs to be said about the exam has been said already, but I will reiterate that while the environment certainly feels more realistic than your run-of-the-mill CTF machine, everything on the exam is in the modules, and on top of that, something from every module is included on the exam. So when people ask:
- What boxes should I do to prepare?
- Will Pro Labs help?
- What other modules should I check out?
Generally speaking, the answer is that everything is in the course, it’s a matter of how well you can figure out your own workflow. Speaking of which, it’s time to get into what I really wanted to talk about with this post.
Methodology is King
Introspection and Reflection
As someone who had experience doing one-off boot2root machines before CPTS, the number one takeaway from the course and the exam is finding my own workflow. Prior to preparing for CPTS, my only real experience with attacking a network was TryHackMe’s Wreath and Holo networks, whatever informal pentesting I did for collegiate competitions, and doing some port forwarding on single boxes. What I think CPTS does very well is not only giving the basics of exploitation, but through how the exercises were designed, forces people into finding a methodology or getting nowhere at all.
If you are someone who is new and scared of these exams like the OSCP or CPTS, I want you to pause for a minute and ask yourself the following:
- How are you choosing to take notes while attacking a network? Does that fit in with when you’re testing systems, or does it feel like a chore/obligation? If you’re not taking notes, what’s your plan while reporting?
- Can you reproduce your results from your notes, or do you have to figure it out every time? Do you know how your pivoting is working and what limitations exist with your setup?
- How are you keeping track of what hosts and credentials you find? How are you managing shells you get back from targets?
- They say attackers think in graphs, but do you even have a graph you’re thinking of in the first place? Can you even find an entry point to your graph?
If you don’t have answers to these questions, or you’re not happy with your answer to a question, great! You’ve identified a gap in your method, and now it’s time to find a solution to that.
Practice Like You Play
I completed the CPTS course months before the actual exam, because I did not want to take the exam and take care of university at the same time. So, back in January, when I was studying for my Security+, I was also taking advantage of a gift card someone gave me at THOTCON to do the Hack The Box Pro Labs, which was definitely the best move after ~4-6 months of little to no hacking. I’ve seen many advise against doing Pro Labs as preparation as they incorporate vulnerabilities and ideas that go beyond the scope of the course, which I agree with.
However, if you need a place to work out the kinks in your workflow and methodology when it comes to researching new things or troubleshooting new tools, working in a new, dedicated lab environment is great. It doesn’t even have to be the Pro Labs specifically- practicing on platforms like VulnLab or even making your own homelab (maybe using GOAD?) give you opportunities to put yourself to the test and identify areas where things aren’t clicking as well. Don’t complete boxes and networks for the sake of completing them, critically analyze what it is you’re doing and think about what things should change so that you figure out solutions quicker.
I spent about 4-5 days working on Dante, and then 9 days working through Zephyr. Dante was a good lab to de-rust with because the network was less about being a network, and more just a bunch of boxes hooked up together, letting you practice pivoting and note-taking. Zephyr, while not necessarily giving the most web practice, was an excellently designed lab to practice Active Directory exploitation, and definitely helped me focus on finding the low-hanging fruit first and optimizing how I used Bloodhound. Regardless of how I felt about these labs, they helped me figure out a nice way to structure my notes, splitting my screen between box-specific notes, the overall topology, and keeping track of the main attack path + commands used to pivot.
I also spent some of this preparation time working on a (scuffed) utility tool called homie. With it being my first time really doing a project in Rust, the code is a bit all over the place, but the point is that investing time into developing ways to optimize and streamline your process is important. Homie is one of many examples of things I have in my arsenal to automate the boring stuff. I have aliases to automate fuzzing vhosts, do nmap scans, copy the IP out of my tun0 interface (a lot of this is thanks to jazzpizazz), and these things definitely pay off.
Thinking in Graphs literally just thinking in the first place
The last major point I’ll make about methodology is on one’s thought process. Everyone starts out as a beginner, and beginners will understandably ask questions that may sound silly. However, I think the biggest problem that plagues a lot of beginners is not truly taking the time to understand things. Maybe part of this reflects the quality of the material they’re reading, maybe this has to do with the way the person chooses to learn.
Let me put it this way.
When presented with a typical XSS tutorial, many people will simply latch on to the payload that gets shown in every tutorial. And maybe they get shown other payloads where additional characters are inserted to fix up broken HTML, or to bypass a WAF.
<script>alert('XSS')</script>
<scr<script>ipt>alert('XSS')</scr<script>ipt>
"><script>alert('XSS')</script>
"><script>alert(String.fromCharCode(88,83,83))</script>
<script>\u0061lert('22')</script>
<script>eval('\x61lert(\'33\')')</script>
<script>eval(8680439..toString(30))(983801..toString(36))</script> //parseInt("confirm",30) == 8680439 && 8680439..toString(30) == "confirm"
<object/data="javascript:alert(23)">
Courtesy: PayloadsAllTheThings
I, like many others who start out, looked at this list and started spraying and praying. Of course, this approach isn’t inherently wrong. Eventually, a payload triggers, and you, the beginner, may be left with the question: “Now what?”
It’s a classic case of being told what to do without understanding why to do it. Sure, you got the injection to work, but did you ever take the time to understand what the inherent vulnerability or impact of XSS is? What are the mechanics at play? Vocabulary/Jargon words like “stored”, “reflected”, and “DOM” might help, but the vocabulary is arbitrary and only serves to describe things more succinctly or descriptively.
I’ve had to go through the process of explaining the significance and mechanics of XSS to people who never truly understood what it’s about multiple times, and the point of this is not to make fun of those people, but to look at a case study of how to learn something.
What good is “thinking in graphs” when you don’t exactly know what to think in the first place?
While writing this, I want to pull out my soapbox and put an end to the “do you need to know to program to work in tech” discourse that circulates every week, but that, of course, is a discussion for another time. The point of this section is to say that in order to hack, in the most basic sense, you have to take the time and understand what it is you’re actually hacking. What components are going into it, and how can you take advantage of primitives to make something unintended happen? This idea alone is, what I think, makes hacking beautiful, and is simultaneously one of the things that flies over a lot of people’s heads who want to give it a shot but give into instant gratification.
Before deviating too far from the main point of this post, I think this video of Bennet Foddy talking over a 1 minute speedrun of his game is something I often bring up when talking about hacking to other people. I think there’s something very similar between the speedrunning community and the hacking community, but I think Foddy describes it best.
“[…] in a way, the role of the speed runner is like the exact opposite of the game designer […] a game designer painstakingly crafts a sculpture out of wood […] the speed runner takes that sculpture and they look it over carefully from top to bottom […] and deeply understand it […] and then, having understood it perfectly, they break it over their knee”

Okay okay back to the exam
I know reading a random person’s thoughts on methodology (especially one who is far from being the best at it) can be a bit of a drag after a little while, so I figured I’d conclude with some final tips for the CPTS exam.
Leave no stone unturned: It’s very easy to run out of ideas and just throw random commands and pray they stick. While that can sometimes work, you will be much more efficient if you create a mental checklist of what it is you want to test. Focusing your efforts and knowing when to move on and maybe circle back is what makes the difference between finding a flag in one day versus five. The only time you’re allowed to give up is when you’ve exhausted all options.
Take breaks: I’m very bad about this one, but to add to the previous point, if you find yourself sitting around doing pretty much nothing, that’s your signal to take a break. And when I say take a break, that means fully giving your mind a break and not doom scrolling YouTube. Some of my biggest breakthroughs happened when I went out on a drive and ran an errand.
Never trust a single tool to do the job: Sometimes tools just miss stuff, and that’s just a natural part of having a bunch of community-built tools. As much as I like using Impacket to do everything remotely, sometimes using Rubeus, PowerView, SharpMapExec, etc. can end up being more effective, and possibly help you get around issues you were having with other tools.
Resetting the environment is not bad: There were at least a few points during the exam that I was pretty sure something was supposed to work, but because of some factor I couldn’t figure out, it wasn’t working. However, two resets later and a slight change in approach, it worked and I was able to progress. If you’re convinced this is the way that was intended, don’t be afraid to reset!
Reference the Material, but also think: I said it earlier, but the exam has at least one concept from each module in the environment, so opening a module and just checking everything it mentions is a valid approach. That said, the environment is built to make sense and not have extremely CTF-y/tricky things. For instance, a random password stored in an alternate data stream in an obscure location on Windows isn’t very realistic, and isn’t likely to show up on the exam. However, based on what you see on machines, you can create an ongoing narrative to understand how things might have been set up (this is a long way for me to say “situational awareness”).
Some Qualms
As much as I enjoyed the CPTS exam experience and certain parts of the course, there are a few issues that I would hope to see get fixed.
100%-ing the course is long: I did the course on a summer break where I wasn’t doing much else, but even then, getting through some of the earlier sections like Nmap, Footprinting, and Vulnerability Scanning were extremely boring, not because the material was bad, but because I already knew what I was doing. When you take the exam, the reason for this rule becomes a little more apparent, but it is still the biggest barrier to completing the exam. As of writing, only a little over 1000 people have fully completed the course at some point, and the course has been out for a year.
Some of the exercises suck: It’s okay for things to suck, that’s just a natural part of life. However, some of these questions can feel unnecessarily long (looking at you Password Attacks and Login Brute Forcing) which is more of a headache if anything. If you get stuck on one of these types of questions, perfectly understandable to ask for help, because sometimes the time is more valuable than guessing at what the one parameter you need to change is.
10 days is a lot: I’m unemployed, so now was the perfect opportunity to take the exam. However, 10 days is a lot, and even though some people say to “treat it like a 20-day exam with a big gap in between”, that’s just a really long period of time for one exam. I could see someone managing to get through this exam while having a full-time job, but you’d have to take more days off than just the weekend if you want it in one attempt.
Cheating and Integrity: As the certification grows, I sincerely hope that HTB is able to manage (1) the quality of the grading process and (2) cracking down on people asking for or selling cheats. With regard to the first point, it took a long time for me, and many others, to get the report graded, and while early reviews of the cert showed detailed feedback even on passing reports, there are some of us who were just told “good job, report is professional”. Hopefully, assuming exam volume increases, they can scale up resources to grading. With regard to the second point, while I do have faith in HTB’s internal processes to crack down on cheating and report selling, I think some of the things I’ve heard from other CPTS holders has been a little concerning. To be clear, I think the number of CPTS holders who have cheated to get the certification is low (saying that the number is zero feels like a wild assumption), but I hope there are more measures taken in the future to really ensure that the integrity of the certification is maintained.
FAQ
On a completely arbitrary scale, how would you rate the difficulty from 1 -10? Quality from 1 - 10?
Course Quality: 8/10 Course Difficulty: π/10
How difficult the course is going to depend on how much you know going into it. I’ve been doing CTFs and learning since 2021, so I knew most of the stuff going in. The growth I experienced from the course was more about refining what I knew and filling in holes, and less about any one thing being difficult. This wasn’t asked, but here are my favorite and least favorite modules:
Favorite: Active Directory Enumeration and Attacks; Windows Privilege Escalation; Pivoting, Tunneling, and Port Forwarding; Attacking Enterprise Networks; File Upload Attacks
Least Favorite: Password Attacks, Login Brute Forcing
How many hours did you spend on the exam?
Apart from the table from earlier, I spent an additional 12-14 hours finalizing my report, mainly because I didn’t take notes on all of the major steps, so I had to go back and redo them.
If you report the full attack chain as you go, the report goes much quicker.
How does CPTS help hiring?
On the sole basis of the name, it doesn’t do much. The cert is new and the name has only just started getting around. Furthermore, while I think a lot of people are hoping this will be a stand-in replacement for OSCP, I think that will take time, as the exam is currently not proctored, and is simply at a natural disadvantage for it if you want to pitch it that way.
I’ve had the most success bringing it up in interviews that I had already gotten, saying “Hey, I don’t have industry experience, but this cert made me do a full penetration test of a small business network and I wrote a report”, which is what starts a conversation. You could also try an apply to Synack Red Team after getting CPTS in hopes of having that on the resume, but I haven’t heard back on my application yet.
How can I pick your brain so I’m also ready for it?
You can DM on Discord @An00bRektn and my hourly rate is $500/hr.
(this is a joke please keep your money)
How do I know when I’m ready for Flags 1 and 9?
cat flag.txt
EZ
Ok but actually
If you got through all of the modules with only minor nudges necessary, and feel like you’ve really engaged with the material, you should be prepared. If you’re like me and still uncertain, drop $50, go do some prolabs, and make sure you have a good flow.
How are you doing?
Fine. Been having some job interviews here and there, but nothing is certain until things are locked in. Hoping to get at least something happening so I can not worry about the balance in my bank account.
(nobody actually asked me this one but I figured I’d ask myself)
Comments